DEM: Non-Persistent VDI Deployment and Backing Up Windows Event Logs

Overview
Some organizations are required to deploy and use SIEM (Security Information and Event Management) products within their environments. Your InfoSec team may live and die by some type of SIEM within your environment whether it be IBM Qradar, Solarwinds LEM, Splunk, LogRhythm, or vRealize Log Insight, etc. However, some environments require that you have copy of “Native” (Original) event logs. These environments believe that “Native” .evtx files are required for legal and general forensics reasons. Some may argue that a SIEM may “Tamper” or “Manipulate” events collected.
Well I happen to work in one these environments. As the InfoSec team felt that logging agent wasn’t enough. We are required to backup windows native .evtx files whenever a client or server is decommissioned. You could imagine the push back for Non-Persistent VDI within our environment, as the Infosec team didn’t feel that logging agent wasn’t enough. I was required to backup .evtx files on every log off for every user who logged onto VDI.
By default non-administrators cannot copy or move the security event logs. This is where DEM (Dynamic Environment Manager) “Privilege Elevation” comes in handy. We can use Privilege Elevation to allow the end user to run a log off script to backup the event logs.
More Info can be found here about Privilege Elevation
Overview of the test environment
- vSphere 6.7 Update 3
- View 7.11
- Windows 1809 (I have tested 1909 and 1903 which had the same issue)
- DEM 9.10
- App volume 4.0 Beta
- Instant Clones
- Desktop Pool – Floating
- Storage: vSAN
PowerShell Script (Example)
Before we begin, I will share the PowerShell script I use. Please make sure you update $BackupPath variable with environments backup location for .evtx files.
Function Backup-UEMEventLog { $SecLog = Get-WmiObject win32_nteventlogfile | where {$.LogFileName -eq “Security”} $SysLog = Get-WmiObject win32_nteventlogfile | where {$.LogFileName -eq “System”} $AppLog = Get-WmiObject win32_nteventlogfile | where {$_.LogFileName -eq “Application”} $FolderDate = Get-Date -Format MM_dd_yyyy $EventDate = Get-Date -Format hhmmss_MM_dd_yyyy $BackupPath = “\esx.lab\uem\UEMEventLog” #Location for Eventlogs. $EventlogService = “EventLog”
IF (Test-Path -Path “$BackupPath$FolderDate”){Write-Host “Folder Exists $FolderDate” -ForegroundColor Green} Else {Write-Host “Folder doesn’t exist…Creating new folder $FolderDate” -ForegroundColor Yellow New-Item -ItemType Directory -Path “$BackupPath$FolderDate”}
#Backups Eventlogs $Seclog.BackupEventLog("$BackupPath$FolderDate$env:COMPUTERNAME$env:USERNAME-Security-$Eventdate.evt") | Out-Null $Applog.BackupEventLog("$BackupPath$FolderDate$env:COMPUTERNAME$env:USERNAME-Application-$Eventdate.evt") | Out-Null $Syslog.BackupEventLog("$BackupPath$FolderDate$env:COMPUTERNAME$env:USERNAME-System-$Eventdate.evt") | Out-Null
#Tests Backup IF (Test-Path -Path “$BackupPath$FolderDate$env:COMPUTERNAME$env:USERNAME-Security-$Eventdate.evt”){Write-Host “SCCUESS: Security Event log $env:COMPUTERNAME$env:USERNAME-Security-$Eventdate.evt exists”-ForegroundColor Green} Else {Write-Host " FAILED: Security Log $env:COMPUTERNAME$env:USERNAME-Security-$Eventdate.evt does’t exist" -ForegroundColor Red} IF (Test-Path -Path “$BackupPath$FolderDate$env:COMPUTERNAME$env:USERNAME-System-$Eventdate.evt”){Write-Host “SCCUESS: System Event log $env:COMPUTERNAME$env:USERNAME-System-$Eventdate.evt exists”-ForegroundColor Green} Else {Write-Host " FAILED: System Log $env:COMPUTERNAME$env:USERNAME-System-$Eventdate.evt does’t exist" -ForegroundColor Red} IF (Test-Path -Path “$BackupPath$FolderDate$env:COMPUTERNAME$env:USERNAME-Application-$Eventdate.evt”){Write-Host “SCCUESS: Application Event log $env:COMPUTERNAME$env:USERNAME-Application-$Eventdate.evt exists”-ForegroundColor Green} Else {Write-Host " FAILED: Application Log $env:COMPUTERNAME$env:USERNAME-Application-$Eventdate.evt does’t exist" -ForegroundColor Red} }
Backup-UEMEventLog
Script location
You will need to place the PowerShell Script in location that End Users are able to read and execute the script from. I chose to place it within our “UEMConfig” location.
Open UEMConfig location
Create a new folder called “Scripts”
Place the PowerShell script within the new “Scripts” folder you just created. I called my Script “UEMEventLog.ps1”
Event Log Location and Permissions
You will need to create a location in order to dump the .evtx files. I have chosen to create another share on my NAS. I then created a folder target under my UEM Namspace called “UEMEventLog”. We will need to configure the Share and NTFS permissions for the End Users. The goal is to make sure when the log off script executes via the End User that they have minimum permissions. We want to make sure they have correct permissions to copy the .evtx and making sure they can’t read .evtx.
NOTE: I am using “Domain Users” for demoing purposes only! Please do not use Domain Users in your production environment.
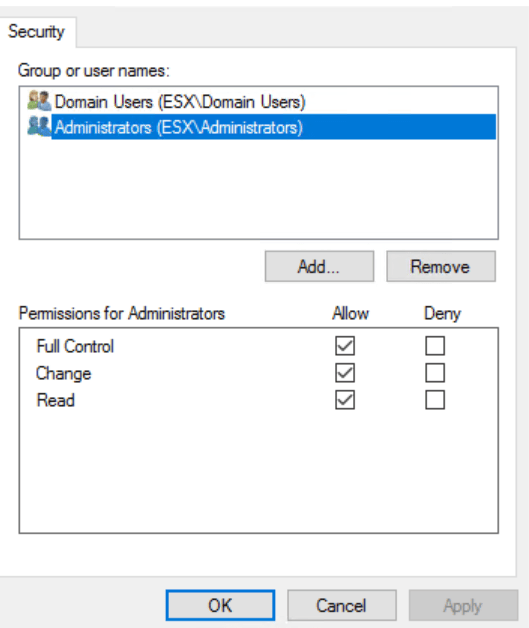
Share Permissions
- Domain Users
- Change and Read
- Administrators
- Full Control, Change, and Read
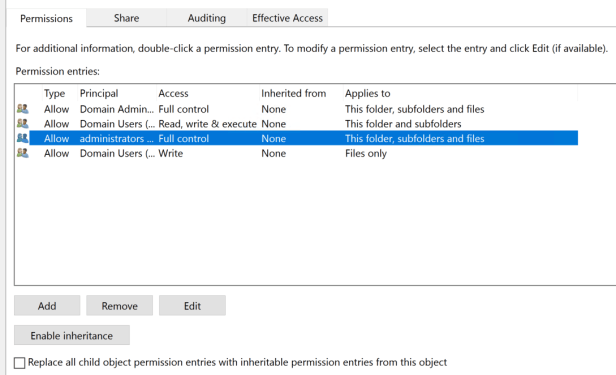
NTFS Permissions
- Domain Users
- Read, Write & Execute – This Folder and subfolders
- Write – Files Only
- Administrators
- Full Control
Configuring Privilege Elevation
Open VMware Dynamic Environment Manager Management Console
Go to User Environment Tab and Select Privilege Elevation
Right Click on Privilege Elevation and select “Create Privilege Elevation Setting”
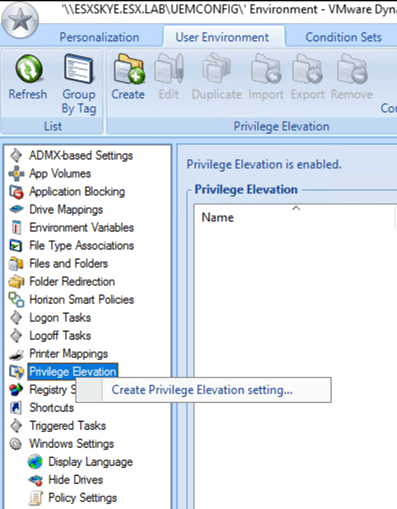
Configure the Following
- Name: Run UEMEventLog
- Type: Argument-Based Elevated Application
- Add
- Executable: C:\Windows\System32\cmd.exe
- Arguments: /c C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -executionpolicy bypass -file \esx. lab\UEM\UEMConfig\Scripts\UEMEventlog.ps1
- Check “Case-Sensitive Arguments
- Check “Also Elevate Child Process”
- Save
NOTE: I chose to use “Case-Sensitive Arguments” as another layer of security. The End user should never really know about this running during log off.
If Case-Sensitive Arguments is enabled you need to make sure the log off argument is exactly the same in GPO. If its not configured exactly the same as the Privileged Elevation settings, it will fail to copy the security.evtx. You can choose to disable “Case-Sensitive Arguments” if you desire.
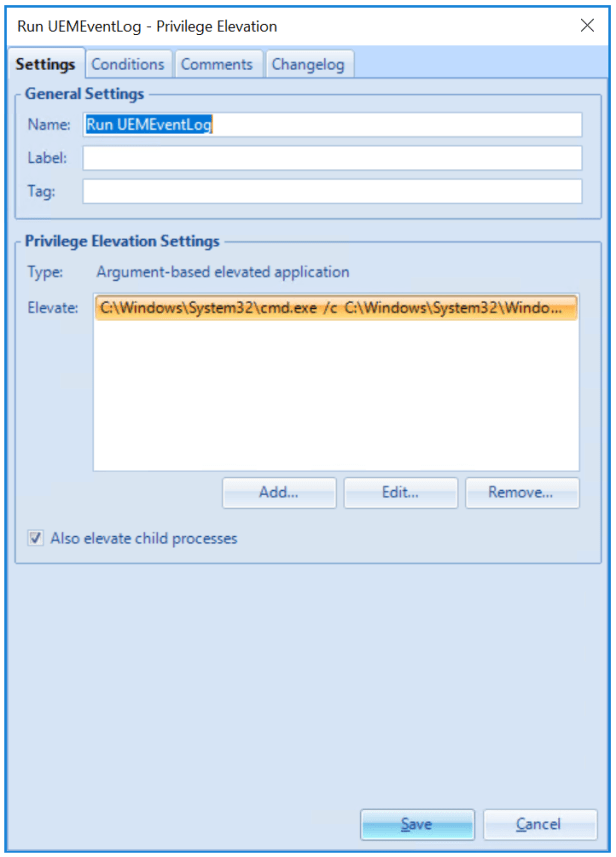
Configuring GPO
By now you are probably wondering why I didn’t choose to use “Log Off Tasks” within User Environment. At first I attempted to use “Log Off Tasks”, I found that when I ran the PowerShell Script manually that Privilege Elevation was working. However, when logging off from a session I found that only the application and system .evtx files copied over. The security .evtx was no where to be found. After running Procmon and look at flexengine.log I found that “FlexEngine.exe” was invoking script. This was causing the End User not having the correct permissions to backup security.evtx. I ended up testing by adding another Privilege Elevation setting for “FlexEngine.exe”. After granting the End User to run “FlexEngine.exe” via Privilege Elevation. The End User was able to copy over Security.evtx. In the end, this was not the route I wanted to take.
After I created a user configuration log off script in the GPO I was able to get Privileged Elevation to run the PowerShell Script correctly.
Note: I chose to add the log off script in my UEM GPO.
Open Group Policy Management Console.
Edit UEM GPO
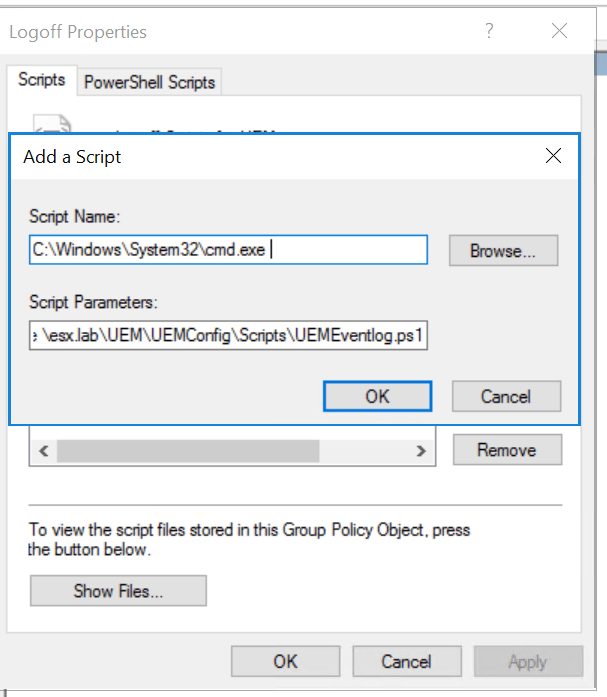
Go to User Configuration –> Windows Settings –> Scripts –> Log Off –> Add
- Script Name: C:\Windows\System32\cmd.exe
- Script Parameters: /c C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -executionpolicy bypass -file \esx.lab\UEM\UEMConfig\Scripts\UEMEventlog.ps1
- Press “OK”
Note: If you choose to use “Case-Sensitive Arguments” make sure that “Script Parameters” matches your Privilege Elevation Arguments.
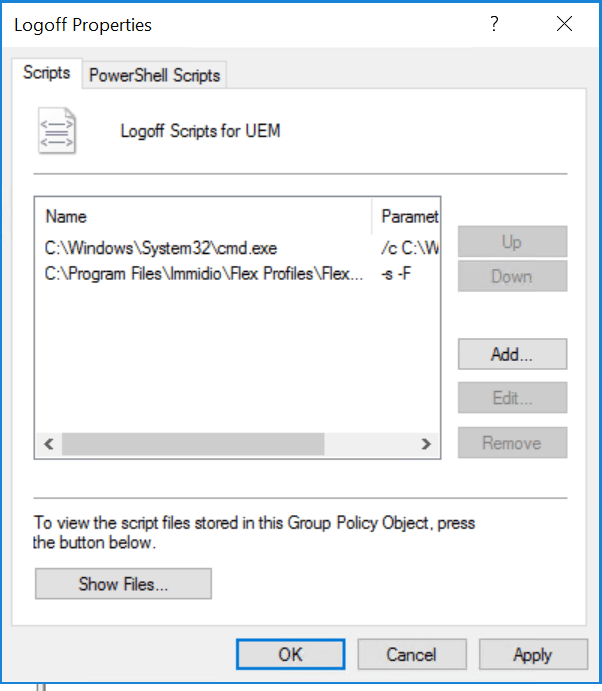
Verify that Event Log Script runs before FlexEngine Log Off Command. If the FlexEngine log off command runs before the Event Log Script, Privilege Elevation will not run.
Lets do some Backing up!
Log on to VDI Desktop Pool with Normal user account (Don’t use Administrator account. This will defeat the purpose of this test since you already have rights.)

After you have made it to the desktop. Lets log off and verify that .evtx files have copied over to the backup location.
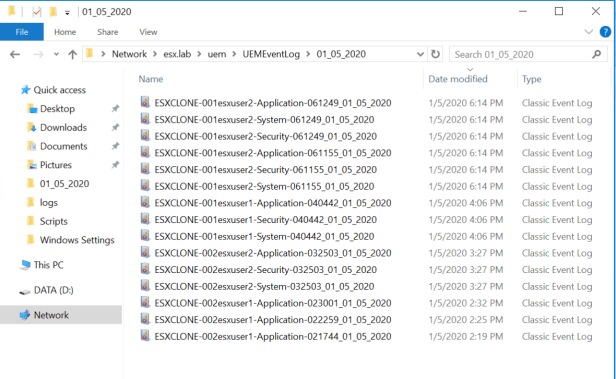
Well look at that! Application, System, and Security copied over to the backup location.